Credit Card fraud, know how you can be prey of it and how to foil the trap of fraudsters.

It was a usual day going for Mr. Aiyyar till he got his credit card bill which had shaken earth underneath him. He got the credit card bill of rupees one lac fifty six thousand and bill had some transaction details which he never made. After contacting bank, he was informed that purchasing were made in a different country which he never visited. What happened with Mr. Aiyyar? Did he become a prey of credit card fraud? Probably yes and there are several people worldwide who become prey of such incident. Card fraud basically involves theft of identity or information on your cards. You, as a credit card holder must know how your information can be used by fraudsters and how to thwart the attempts of such people to steal your information. The stealing can take place in one of the following ways:

Card trapping – This involves attaching a data skimming device in the card reader slot to copy information from the magnetic strip when one swipes the card. Fraudsters also set up cameras near the machine to get the PIN. There are internal people involved in stealing the information and your card is cloned when you insert your card in swipe machine or any ATM. The information is retrieved later and is used to do transactions. When you know about such fraud, it becomes too late and as a card holder, you become liable to pay the bill.
How to prevent it – Get your card swiped in your presence and observe if any device is attached with the card swipe machine. Periodically change your card PIN especially when you feel something suspicious. Be attentive when your card is being swiped and do not divert your attention in phone calls or looking here and there. You might be deliberately tried to get your attention diverted by the people involved in such practices so that their purpose get meet.

Shoulder surfing – If you find friendly bystanders in the room or outside who try to help you if your card gets stuck or peer over your shoulder, beware. They are there to get you to reveal your PIN. Not everyone is dishonest or racketeer but you have to conceal the information which is required to be confidential. Hide the keys of the machine while entering your PIN. If you feel your PIN has been observed by someone, immediately change it. Some people write their PIN on ATM or credit card and in case card is lost, it becomes golden opportunity for fraudsters to use it for any purchasing.
The ease of e-shopping or online bill payment is matched by the felicity with which identity theft can be carried out on computer or smartphone. Mumbai based Narayan Shinde knows it well. He was in his office when he got alerts about online transactions abroad made using his credit card. There are various ways this card information could have been stolen.
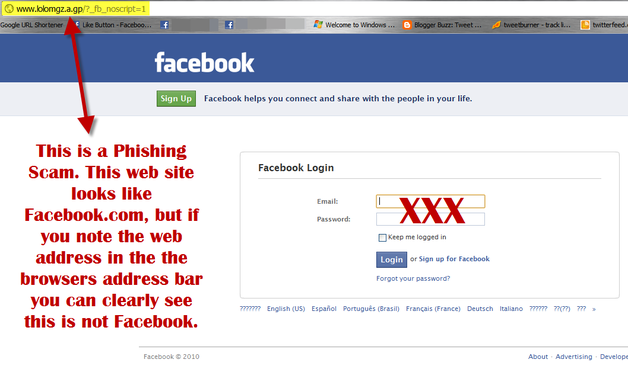
Pharming – In this technique, fraudsters reroute you to a fake website that seems similar to the original. So, even as you conduct transactions and make payment via credit or debit card, the card details can be stolen. Better to be attentive while using your card for online transactions and ensure your transaction is being done on the authentic website, not the fake one. Never click on any pop up and block pop ups in the browser.
Keystroke logging – Here, you unintentionally download a software, which allows the fraudster to trace your key strokes and steal passwords or credit card and Net banking details. Prefer to use virtual keyboard while entering password or any crucial information. Do not allow any software to get install in your phone or computer. Sometimes you are offered an alluring benefit for installing an application, check the source of such application and install firewall with your system so that unnecessary application could not be installed.
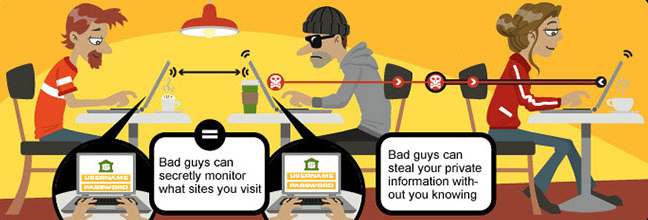
Public Wi-Fi – If you are used to carrying out transactions on your smartphone, public Wi-Fi makes for a good hacking opportunity for thieves to steal your card details. While using a public network, your browsing history is stored in cache memory which can be easily retrieved by the people involved in fraud practices. Better is not to use public Wi-Fi and use your own internet with security functions activated.
Malware – Malware is a malicious software which tries to infect a computer or mobile device. Hackers use malware for any number of reasons such as, extracting personal information or passwords, stealing money, or preventing owners from accessing their device. You can protect yourself against malware by using anti-malware software.

How to prevent malware – Use powerful antivirus and anti-malware software and don’t open email attachments from unknown or unexpected sources.
Merchant or point of sale theft – This is perhaps the most effective form of stealth, wherein your card is taken by the salesperson for swiping and the information from the magnetic strip is copied to be illegally used later.

Phishing & vishing – While phishing involves identity theft through spam mails which seem to be from a genuine source, vishing is essentially the same through a mobile phone using messages or SMS. These trick you into revealing your password, PIN or account number. Never reveal your confidential information such as card number, its expiry date, CVV number or One Time Password-OTP with any person claiming to be representative of bank. Bank personnel never ask for such detail from its customers. Better to ignore such calls, SMS and emails.
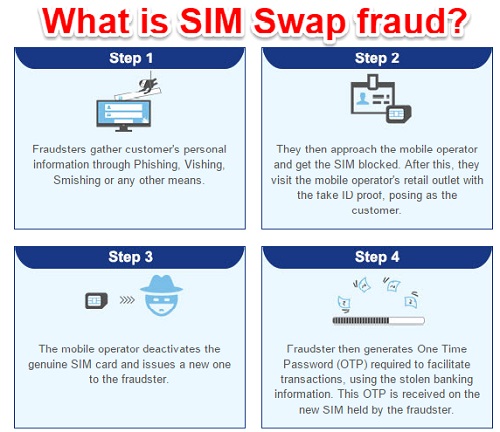
SIM swap fraud – Here the fraudster contacts your mobile operator with fake identity proof and gets a duplicate SIM card. The operator deactivates your original SIM and the thief generates one-time password (OTP) on the phone to conduct online transactions. Keep your ID proof in safe custody and never hand over your ID proof to any stranger for Xerox or other purposes, your ID card can be used for issuing a duplicate SIM or can be used to make any financial transaction. If you ever see your phone having SIM registration failed, immediately call your operator to make sure your SIM is not being misused.
Unsafe apps – Mobile apps other than those from established stores can gain access to information on your phone and use it for unauthorized transactions. Usually people get a link through SMS to download an application with lucrative offers of free product or services. Never blindly install such application else your all secret information can get accessed to fraudsters.
This is how you can thwart malpractices of fraudsters. You are always under surveillance of people who want to steal your secret information and you all monetary transactions are being monitored by them. A small mistake of your can be very fatal resulting huge loss which you are liable for. Be alert, be attentive and secure your confidential so that no body could preach into it.

 Currency Convertor
Currency Convertor Post an article
Post an article Covid19 Updates
Covid19 Updates Prashant Singla, Axis Bank.
Prashant Singla, Axis Bank.







 sending...
sending...




